First 4 CVEs
My first 4 CVEs from vulnerability hunting.
I’ve been practicing vulnerability hunting for two weeks and wrote simple PoCs for my findings. I’m happy that I already got 4 CVEs.
Note: These four CVEs are small achievements, since they’re something anyone can do. I just wanted to record them as milestones, even though they’re not as major as CVEs from companies like Microsoft, NASA, Apple, and others.
Table of Contents
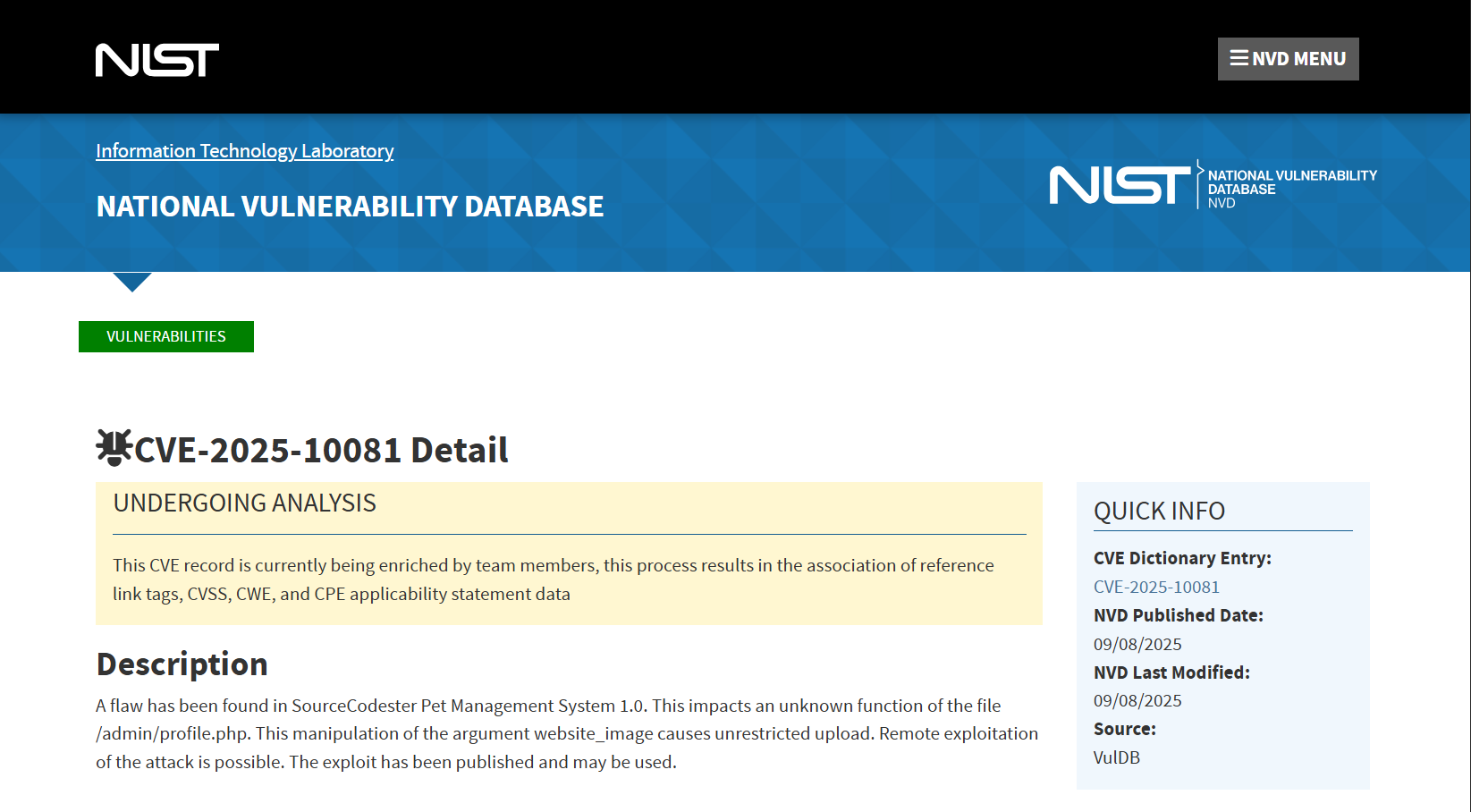
CVE-2025-10081
Pet Management System 1.0 /admin/profile.php website_image unrestricted upload
A vulnerability was found in SourceCodester Pet Management System 1.0. It has been rated as critical. Affected by this issue is an unknown function of the file /admin/profile.php. The manipulation of the argument website_image with an unknown input leads to a unrestricted upload vulnerability. Using CWE to declare the problem leads to CWE-434. The product allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product’s environment. Impacted is confidentiality, integrity, and availability.
The advisory is shared for download at github.com. This vulnerability is handled as CVE-2025-10081. The exploitation is known to be easy. The attack may be launched remotely. The exploitation needs additional levels of successful authentication. Technical details as well as a public exploit are known. The MITRE ATT&CK project declares the attack technique as T1608.002.
The exploit is available at github.com. It is declared as proof-of-concept. By approaching the search of inurl:admin/profile.php it is possible to find vulnerable targets with Google Hacking.
There is no information about possible countermeasures known. It may be suggested to replace the affected object with an alternative product.
The vulnerability is also documented in the vulnerability database at EUVD (EUVD-2025-27106). Entries connected to this vulnerability are available at VDB-289709, VDB-298426, VDB-298902 and VDB-303261.
Click this link for the Proof of Concept
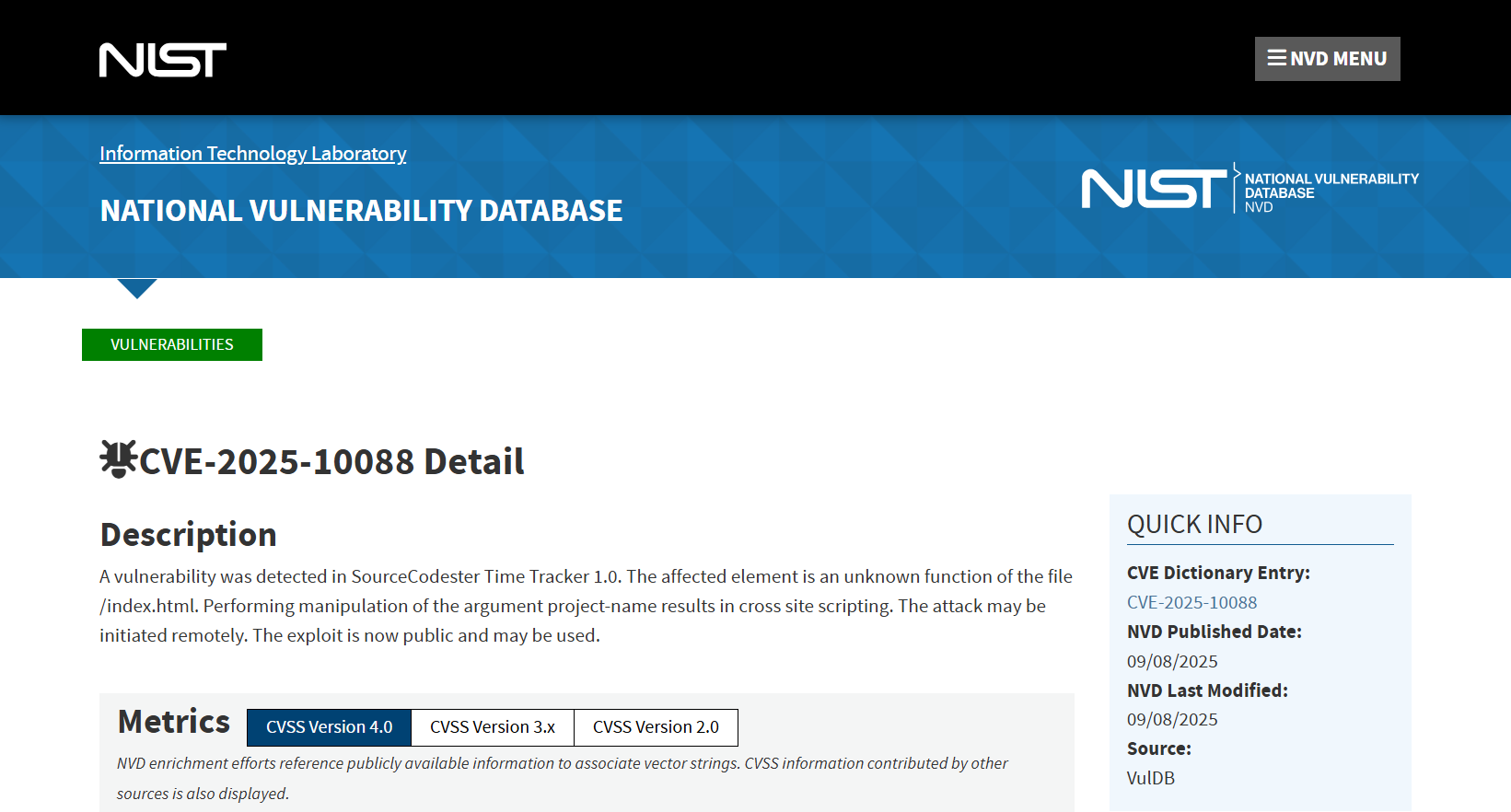
CVE-2025-10088
Time Tracker 1.0 /index.html project-name XSS
A vulnerability was found in SourceCodester Time Tracker 1.0. It has been declared as problematic. This vulnerability affects an unknown functionality of the file /index.html. The manipulation of the argument project-name with an unknown input leads to a cross site scripting vulnerability. The CWE definition for the vulnerability is CWE-79. The product does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users. As an impact it is known to affect integrity.
The advisory is shared for download at github.com. This vulnerability was named CVE-2025-10088. The exploitation appears to be easy. The attack can be initiated remotely. Successful exploitation requires user interaction by the victim. Technical details and also a public exploit are known. The MITRE ATT&CK project declares the attack technique as T1059.007.
It is possible to download the exploit at github.com. It is declared as proof-of-concept. By approaching the search of inurl:index.html it is possible to find vulnerable targets with Google Hacking.
There is no information about possible countermeasures known. It may be suggested to replace the affected object with an alternative product.
The vulnerability is also documented in the vulnerability database at EUVD (EUVD-2025-27113). The entries VDB-164988, VDB-170600, VDB-173008 and VDB-184377 are related to this item.
Click this link for the Proof of Concept
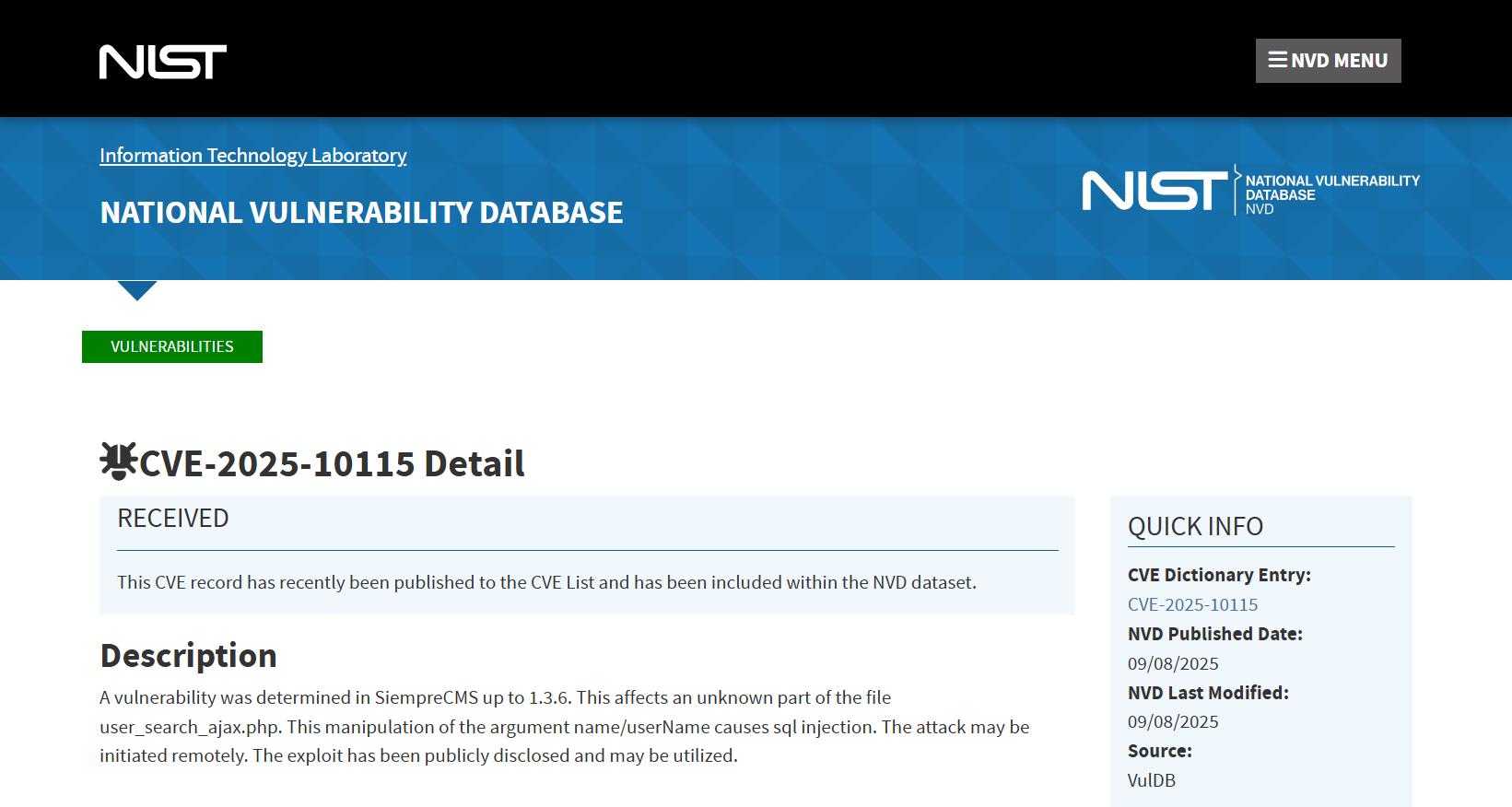
CVE-2025-10115
SiempreCMS ≤1.3.6 user_search_ajax.php SQL Injection
A vulnerability, which was classified as critical, has been found in SiempreCMS up to 1.3.6. Affected by this issue is some unknown processing of the file user_search_ajax.php. The manipulation of the argument name/userName with an unknown input leads to a sql injection vulnerability. Using CWE to declare the problem leads to CWE-89. The product constructs all or part of an SQL command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended SQL command when it is sent to a downstream component. Impacted is confidentiality, integrity, and availability.
The advisory is shared for download at github.com. This vulnerability is handled as CVE-2025-10115. The exploitation is known to be easy. The attack may be launched remotely. No form of authentication is required for exploitation. Technical details as well as a public exploit are known. The MITRE ATT&CK project declares the attack technique as T1505.
The exploit is available at github.com. It is declared as proof-of-concept. By approaching the search of inurl:user_search_ajax.php it is possible to find vulnerable targets with Google Hacking.
There is no information about possible countermeasures known. It may be suggested to replace the affected object with an alternative product.
The vulnerability is also documented in the vulnerability database at EUVD (EUVD-2025-27193). The entries VDB-116130 and VDB-304298 are related to this item.
Click this link for the Proof of Concept
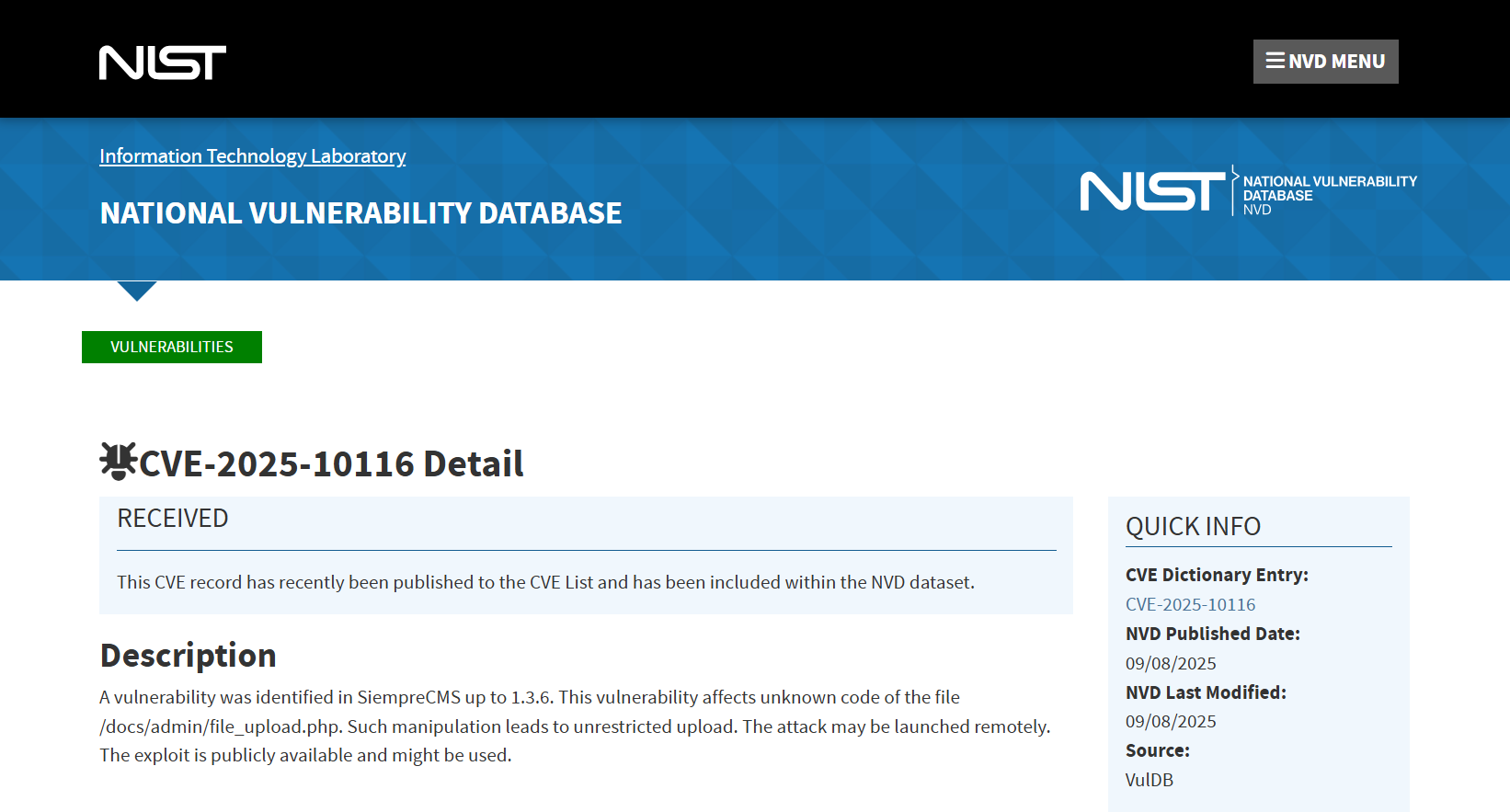
CVE-2025-10116
SiempreCMS ≤1.3.6 file_upload.php unrestricted upload
A vulnerability, which was classified as critical, was found in SiempreCMS up to 1.3.6. This affects an unknown function of the file /docs/admin/file_upload.php. The manipulation with an unknown input leads to a unrestricted upload vulnerability. CWE is classifying the issue as CWE-434. The product allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product’s environment. This is going to have an impact on confidentiality, integrity, and availability.
The advisory is shared at github.com. This vulnerability is uniquely identified as CVE-2025-10116. The exploitability is told to be easy. It is possible to initiate the attack remotely. No form of authentication is needed for exploitation. Technical details and a public exploit are known. MITRE ATT&CK project uses the attack technique T1608.002 for this issue.
The exploit is shared for download at github.com. It is declared as proof-of-concept. By approaching the search of inurl:docs/admin/file_upload.php it is possible to find vulnerable targets with Google Hacking.
There is no information about possible countermeasures known. It may be suggested to replace the affected object with an alternative product.
Similar entry is available at VDB-323084.
Click this link for the Proof of Concept